Command line Utilities for the Administrator:
plb – “plist broker” can visualize a plist in a like my tool jpt does for JSON. plbplx the plist extractor is a minimal version for extraction only. Both are shell scripts and functions you can incorporate into your own scripts, like my other embeddable tools: jpt, ljt, jse and shui
Github project page: plb
Tagged blog posts: tag/plb
clui – “command line Unicode info” is like the built-in Character Viewer for the macOS Terminal, get info about any Unicode character. Search for them by description or component character. Get the Code Point, descriptions (Unicode and/or Apple), UTF-8, 16, or 32 encodings. Can output results in several formats: plain text, CSV, JSON, and RTF.
Github project page: clui
Tagged blog posts: projects/clui
ljt – The “little JSON tool” is a safe and easy way to parse JSON and retrieve values natively in your shell scripts, no external dependencies required! Like the jpt it too is a shell script that leverages the Javascript binary jsc, however unlike the jpt, this little JSON tool only gets values, nothing else. This keeps it nice and small and easily embedded into your shell scripts, the minified function is a scant 1.9k
Github project page: ljt
Tagged blog posts: scripting/ljt/
jpt – the “JSON Power Tool” is a Javascript and shell polyglot script that leverages jsc, the JavascriptCore binary that is standard on every Mac since 10.4! Since the jpt is purposefully written in ES5 to maintain maximum compatibility, then why yes, this tool does run on both PPC and Intel Macs all the way back to OS X Tiger and then all the way forward to the latest macOS! Many Linux distros like CentOS and Ubuntu come with jsc pre-installed also, even Windows with the Linux Subsystem installed can run jsc and therefore can (usually) run the jpt!
What you can do with the jpt? Query JSON documents using either the simple yet expressive JSONPath syntax or the singular and precise JSON Pointer (RFC6901) syntax. The output mode is JSON but additional creative output modes can render JSONPaths, JSON Pointer paths, or even just the property names with their “constructor” types (try -KC with -J or -R) Textual output can be encoded in a variety of formats (hex/octal/URI encoding, Unicode code points, etc…), data can be modified using both JSON Patch (RFC6902) operations (add, replace, remove, copy, move, test) and also JSON Merge Patch (RFC7386) operations. JSON can be worked with in new ways, try -L for “JSONPath Object Literal” output to see what I mean. Or you simply feed jsc a file to pretty-print (stringify) to /dev/stdout. I’ll be writing more about this one for sure.
Github project page: jpt
Tagged blog posts: scripting/jpt
shui – first-class Applescript dialog boxes in your shell scripts without needing to remember esoteric Applescript phrasings! If you think it’s odd for code to have possessive nouns and are more comfortable in shell, you’re not alone. shui can be embedded in either bash or zsh scripts but it can also output Applescript if you really want to know how the sausage is made or want to embed in your script without shui. Hopefully shui will let you forget those awkward Applescript phrasing and focus on your shell script’s features and functionality. It uses osascript to execute the Applescript and launchctl to invoke osascript in the correct user context so user keyboard layouts are respected (vs. root runs). Check out the project page for demo videos and then give shui a try.
Project page: shui
Tagged blog posts: scripting/shui
shef – Shell Encoder and Formatter – Transform arbitrary text into 7-bit ASCII using a variety of shell encoding and quoting styles. Output can be used in shell scripts or passed into shell script by other tools that don’t require shell quoting. Useful for systems that don’t support 4-byte UTF-8 encoded characters.
Project page: shef
Tagged blog posts: projects/shef
ppdOptionsDiff.command – Compares the stock PPD (in /Library/Printers) with the installed PPD (/etc/cups/ppd) to produce “-o” options for use with lpadmin (see article here)
setUserTemplateDefaultDocks – For the Jamf Pro admin, this will copy the localized default.plist from inside Dock.app to the appropriate localized User Template folder, adding a GUID and file-label to each entry to satisfy the Jamf Pro Dock Item payload code that looks for these elements when adding or removing icons. Failing to add these Jamf Pro will nuke the default.plist FYI
RemoveItemFromDock – Command line utility to remove items from the dock
AddItemToDock – Command line utility to add items to the dock.
AddLoginItem – Command line utility to add items to users’ login items
createRecoveryHDUpdater 15.4.6.command – built PKG now is targetable to volumes other than / (Note: Recovery HD updater packages for 10.11 will only work when run in OS X 10.11, previous packages could run in different OSes not so for 10.11). This is only useful for HFS+ formatted disks. APFS need not apply (it will make an HFS+ partition on your APFS disk BTW)
Widgets for Wonks:
Rebuilt with Platypus (5.3) these 64-bit menubar apps will still run on Catalina, however they are un-notarized and unsigned. But why trust me or Apple, if you want to know what the do just look inside at the bash script that makes it tick.
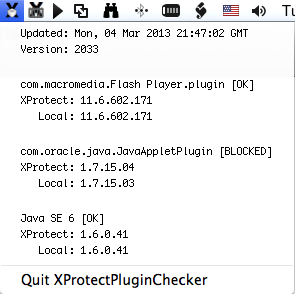
XProtectPluginChecker – Quickly survey the status of Java, Flash, and any other Plug-Ins Apple deems insecure and unworthy of your usage.
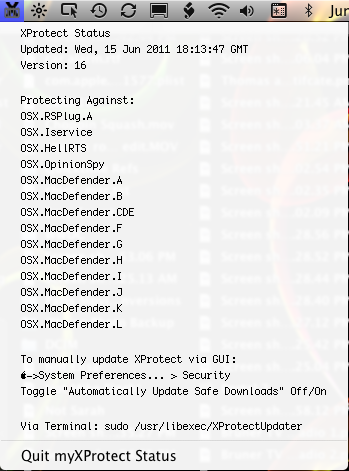
myXProtectStatus – A drop down status menulet, showing date, version, and threats protected against in the Xprotect plist. Written in bash, wrapped by Platypus, it is informational only (so don’t ask me to add some menu item to do something, it just reports). Tuck it away somewhere and add to your loginitems.
Screenshot of myXProtectStatus:
Exercises in Applescript :
If you have OS X 10.5 you’ll think this is neat… you’ll also be on a very old computer…
ToggleDock – Toggle the Dock appearance from “glass” to “no glass” when in horizontal mode.
I like your widget so I tried myXProtectStatus but it gives an error. ‘Can’t make “Oct” into type integer’ I am running Mac OS X 10.7.2.
Never mind. Today it works. Odd. Thanks, its great.
Hi, I am trying to use your “removeitemfromdock” application to remove face time and the app store but when I install the .pkg you’ve provided nothing actually installs into the /sbin folder so when I try to run the command from terminal I just get “command not found”. This is on 10.7.4.
I’ve been beating my head against the wall trying to remove the Facetime.app from the default dock and I’ve tired everything, editing default.plist, copying a com.apple.dock.plist to the User template folder, etc. none of them seem to work so this is my last resort.
Any help would be awesome!
Hi Matt,
Thanks for pointing that out. The RTF in the PKG was not correct, it is actually installed in /bin. Since that is in the search path you need only type removeitemfromdock and it will be found, but feel free to prepend /bin/ if you wish :)
Also, for those looking to modify the default Dock in 10.7 it is located here now, in a plist:
/System/Library/CoreServices/Dock.app/Contents/Resources/English.lproj/default.plist
So to kill FaceTime for all new users you can use this form to edit the default Dock in 10.7:
sudo removeitemfromdock -f /System/Library/CoreServices/Dock.app/Contents/Resources/English.lproj/default.plist /Applications/FaceTime.app/
I have updated the Readme file in the installer and added some bug fixes also.
Todo: _CFURLString is a file:// URL when your home folder is on another volume
You sir, are awesome!
You made my day with your createRecoveryHDUpdater.command ! So nicely authored, so well documented. Saved me from the lame tips of “Install OS X over your installation for Recovery HD recover”. No cheesy guys, i don’t want my nicely defragmented OS X partition get overwritten all over again.
Kudos and respect from Greece,
Vaggelis
The article regarding “createRecoveryHDUpdater.command” was really very helpful, when I decided to grant my old MacMini from 2006 with Lion (yes, changed the CPU to a Dual Core, so a new installation of Lion is very complicated) a 120 GB Samsung SSD.
1. Connect SSD via USB or Firewire
2. Prepare the SSD with Hard disk Utility with HFS+
3. Activate owner on the SSD with “sudo /usr/sbin/vsdbutil -a /Volumes/nameOfSSD”
4. Clone the internal harddisk to SSD with SuperDuper (command line utilities should work, too, but ditto failed in my case).
5. Try, if you can boot from external SSD (reFit is very helpful).
6. If yes, reboot the internal disk again and create the recovery partition with “RecoveryHD Updater.command” created by the above mentioned tool. Tata! It worked perfectly.
I built in the SSD instead of the old internal disk and all went fine. The performance yield is impressive. The SSD is perfect configured without new installation.
Thanks a lot from Krefeld, Germany
Erich
Hi- stumbled across your utility via ivanexpert.com.
Thanks for the script; helped get a Macbook Air ‘mid-2013’ away from always running ‘internet recovery mode’ when all the user needed to do was perform a Disk Utility/Repair Disk procedure.
Couple of requests-
1) since the script runs ‘under’ windows that it opens it would be nice if it wrote a log file that could be reviewed afterwards. Could especially be helpful for new OS X releases, ‘strange’ configurations, etc.
2) At the beginning of the script it would be nice to notify the user-
+ if the recovery partition exists and if so what OS X recovery version is on this partition?
+ What OS X version will be installed vs what version is currently installed.
I’m a Finderless XFile user that got turned on to your XProtectPluginChecker via Rixstep. I guess I’m really extreme, and disabled SpotLight shortly after it was released a few OS versions ago. Ergo, XProtectPluginChecker didn’t work for me until I modified its ‘checkPlugin’ function, like so:
function checkPlugin
{
pluginBundleName=”$1″
#use spotlight to return result then grep for Internet
pluginBundlePath=$(mdfind “kMDItemCFBundleIdentifier == ‘$pluginBundleName'” | grep “Internet Plug-Ins”)
# add section for those of us who shun StopLight
if [ -z “$pluginBundlePath” ]; then
foo=”$(IFS=$’\n\b’;echo “$pluginBundleName” | sed -e ‘s/\.plugin$//g’ -e ‘s/^.*\.//g’ -e ‘s/$/\.plugin/1’)”
pluginBundlePath=”$(find ~/Library/Internet\ Plug-Ins /Library/Internet\ Plug-Ins -name “$foo” | head -1)”
fi
#get values from XProtect and local version, etc.
Here’s to sharing and caring; THANKS to you!