Updated: I’ve linked text files of string dumps to the binaries thoughout the article, I suppose not everyone wants to install and run the code to find out themselves! :D
Another OS X malware media darling is out there, but it’s not the DNS changing kind that RSPlug-F was. Rather this one has a lot more code in it, active code that is watching keystrokes, monitoring AIM, MSN, Yahoo, and iChat messengers and more.
So I found a sample (this is the actual installer careful, folks) in the MishInc FLV To MP3 converter. Which is just a .jar file, put .zip at the end and you can see the guts when expanded. However, it’s a self extracting installer using iZPack so it’s easier just to run it and let it unpack. Here’s some screenshots:
Nothing much in there
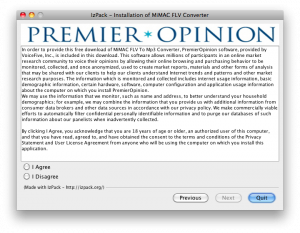
Jackpot on the 2nd screen, here’s the goods. Note, if you click I disagree, the software is not installed! Not too mal. Here’s the text from VoiceFive‘s agreement:
In order to provide this free download of MiMAC FLV To Mp3 Converter, PremierOpinion software, provided by VoiceFive, Inc., is included in this download. This software allows millions of participants in an online market research community to voice their opinions by allowing their online browsing and purchasing behavior to be monitored, collected, and once anonymized, used to create market reports, materials and other forms of analysis that may be shared with our clients to help our clients understand Internet trends and patterns and other market research purposes. The information which is monitored and collected includes internet usage information, basic demographic information, certain hardware, software, computer configuration and application usage information about the computer on which you install PremierOpinion.
We may use the information that we monitor, such as name and address, to better understand your household demographics; for example, we may combine the information that you provide us with additional information from consumer data brokers and other data sources in accordance with our privacy policy. We make commercially viable efforts to automatically filter confidential personally identifiable information and to purge our databases of such information about our panelists when inadvertently collected.
By clicking I Agree, you acknowledge that you are 18 years of age or older, an authorized user of this computer, and that you have read, agreed to, and have obtained the consent to the terms and conditions of the Privacy Statement and User License Agreement from anyone who will be using the computer on which you install this application.
Does anyone else find it odd that they say your info is anonymized, but then go on to use an example of information they monitor is name and address?! But not worry, commercially viable efforts will be used to filter that out. Does that mean if it’s too expensive they won’t bother doing a really good job? Nonetheless for this installer, if you say I Disagree you are able to continue to install the MP3 converter without PremierOpinion installing.
But let’s say: I agree for the heck of it :)
First it drops two files in /private/tmp: script.sh which simply makes the other file, poinstaller, executable. If you are connected to the internet it then downloads two folders: installtmp and tapinstaller, both folders have the exact same binary called PremierOpinion(496KB), installtmp has a different sized poinstaller binary and tapinstaller contains upgrade.xml, which contains a link to a file called rule14.xml, found on a server at post.securestudies.com. Downloading rule14.xml from them you get a link to the latest PremierOpinion.zip and the version numbers of the expected support libraries and essential files.
pointsaller has some Applescript to open the survey window in Safari and things like getting “campaign ids”, doing shell scripts with admin privileges, references to MacSniffer (a TCP packet sniffer), and more. Also while looking at the strings of poinstaller you’ll find reference not only to post.securestudies.com found but also it.kingroutecn.com which has the same rule14.xml but instead of PremierOpinion you get PermissionResearch. Doing some digging, it can be discovered that VoiceFive, Permission Research (which has many screensavers to download), and Premier Opinion are all in the same network block as ComScore, a multi-headed hydra of consumer buying insight.
Now back to the Chinese server (which is not used to download the payload, perhaps, only in China?) digging it.kingroutecn.com gives you 218.108.8.85, doing a reverse lookup gives hidden-master.hzman.net, doing a reverse lookup gives you 127.0.0.1 that is you!? Whois on it.kingroutecn.com and hidden-master.hzman.net will point to Hangzhou, China, a very big city just southwest of Shanghai (it looks smoggy in Google Maps). The question is why are their two similar packages being served from the US and China? And why is the Chinese version newer (2.3.0.69 vs. 2.2.0.59)?
Anyway, Woodward and Bernstein aside, during all this unpacking of files in /private/tmp an authentication window asking for system.privelege.admin, that is to say, it wants root privileges. If you say yes, you’ll get a launchd daemon running as root installed to /Library/LaunchDaemons/PremierOpinion.plist, it’s an on-demand daemon that will respawn the PremierOpinion process if you try killing it in Activity Monitor. Respawning calls the RunPremierOpinion.sh script from /Application/PremierOpinion folder, it checks to see if you have Access for Assistive Devices enabled this is essential to logging your keystrokes. It does this by simply touching /private/var/db/.AccessibilityAPIEnabled, which can only be done by root, but it’s already running as that no prob! What’s weird about this file is that when you turn on Access for Assistive Devices via the GUI in System Preferences it creates the file with the single character ‘a’ but OS X will still activate the service if the file is created and is 0 bytes. After installing a Safari window will pop up asking you who uses the computer, the ages of the folks using it, and other tidbits, you can see here. When this app upgrades itself you will find a folder at /private/tmp/autoupgrade which has the same contents of /Applications/PremierOpinion.
So /Applications/PremierOpinion has quite a few things inside, libraries, scripts, and an Uninstaller (?!), and PremierOpinion.app. Inside the app is some Code Signing, the binary (a much bigger 3.6MB version), and in Resources it contains survey.nib, systemtray.nib and InjectCode.app, which inside has code from Jonathan Rentzsch used for mach code injection*, taken from Growl’s 1.2 source code and recompiled by user huangxianghua as seen in the string: /Volumes/10.5/Users/huangxianghua/Downloads/Growl-1.2-src/external_dependencies/mach_star/mach_inject_bundle/mach_inject_bundle
Further and further down the rabbit hole, but let’s just run the Uninstaller. It deletes the folder in Applications but the process remains as well as the LaunchDaemon and all the files in /private/tmp, however on reboot the process is indeed not running, /private/tmp is cleaned out, but the LaunchDaemon and Assistive Access remains on.
So here’s an uninstall script of my own (disconnect all network conections first, in case it is logging keystrokes, it might grab your password):
sudo launchctl unload -w /Library/LaunchDaemons/PremierOpinion.plist
sudo rm /private/tmp/poinstaller
sudo rm /private/tmp/script.sh
sudo rm -rf /private/tmp/installtmp
sudo rm -rf /private/tmp/autoupgrade
sudo rm -rf /private/tmp/tapinstaller
sudo rm -rf /Applications/PremierOpinion
sudo rm /private/var/db/.AccessibilityAPIEnabled
That should do it.
For extra insight, try running the PremierOpinion or PermissionResearch binary from the command line as root, there is all sorts of info to be found when it writes to stdout, such as when it starts a service port 8254: 2010-06-03 15:59:06.175 PermissionResearch[1658:60f] Starting server on port 8254 and, surf around a little, it’ll report on the YouTube videos you are watching and other things it deems interesting.
Extra extra credit run a Sample on it from Activity monitor and see what it’s doing: FileInventoryTask::MainTask(void*), file inventory eh, that’s why it’s eating up 30% of my CPU!
Hmmm, enough rabbit hole adventures for today, comments are welcome.
Oh yes, and PowerPC folks don’t worry, they didn’t compile for PPC :)
*Update:
To go on further about the injection aka Method swizzling code. This is where you have your code respond to a message call instead of the original code, the power in this is that you can get in the middle of the internal calls and do what you will with their data but then pass them on to the original method. So they probably are swizzling methods in Safari or perhaps at the network layer so they can see what you are downloading, watching, etc. Combined with packet sniffer ‘all your data are belong to them’. However please take note that these the reason this app can do this is because you’ve given them the keys to the castle by authenticating it as root, the technologies it’s leveraging aren’t inherently nefarious, rather fundamental and and essential to system operation, if root can’t do it then who can? This is where either it falls on the user or the OS needs to be better about protecting the user from themselves, perhaps the OS could sandbox downloaded apps with very restrictive settings, alerting you when it attempts something privileged, although this can desensitize a user quickly to clicking Agree. Nonetheless this is a defining conundrum of this century. The power of personal computers is being subverted for the nefarious gain of others and we need to defend against it, the era of curated computing might be ushered in because of this. We’ve seen it so many times, when good things get used for bad purposes, there’s a sea change. Crises precipitates change.